AWS Verified Access
- What is AWS Verified Access
- What does AWS Verified Access bring?
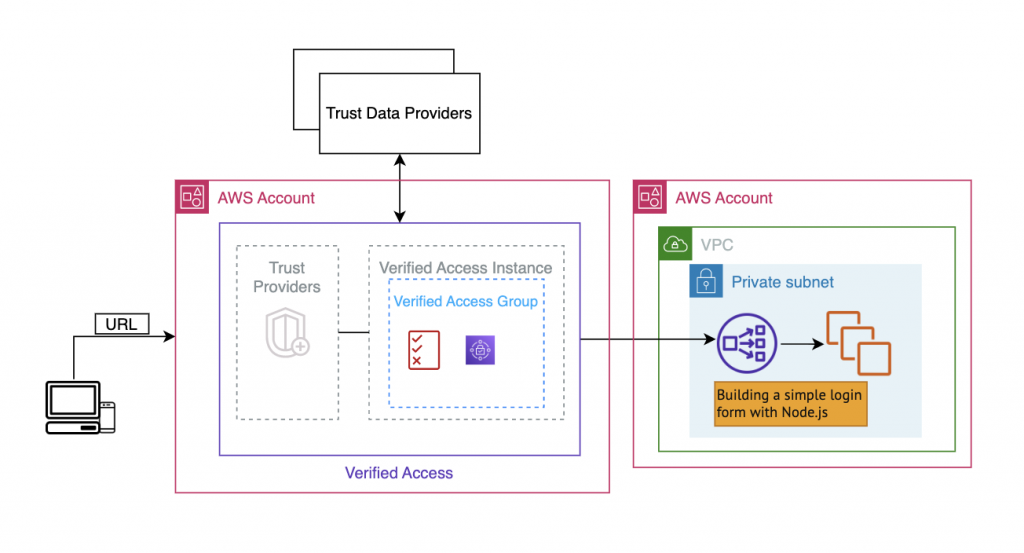
- Overview the High Level Design
- Use scenario for Verified Access
- What is zero trust?
- What is zero trust architecture?
- Pricing?
- AWS Verified Access Elements
- Verified Access Instances
- Verified Access Trust Provider
- Verified Access Group
- Verified Access Endpoint
- Verified Access policies
What benefits does Verified Access bring?
- Improved security posture – A traditional security model evaluates access once and grants the user access to all applications. Verified Access evaluates each application access request in real time. This makes it difficult for bad actors to move from one application to another.
- Integration with security services – Verified Access integrates with identity and device management services, including both AWS and third-party services. Using data from these services, Verified Access verifies the trustworthiness of users and devices against a set of security requirements and determines whether the user should have access to an application.
- Improved user experience – Verified Access removes the need for users to use a VPN to access your applications. This helps reduce the number of support cases arising from VPN-related issues.
Simplified troubleshooting and audits – Verified Access logs all access attempts, providing centralized visibility into application access, to help you quickly respond to security incidents and audit requests.
How Verified Access works
AWS Verified Access evaluates each application request from your users and allows access based on:
- Trust data sent by your chosen trust provider (from AWS or a third party).
- Access policies that you create in Verified Access.
When a user tries to access an application, Verified Access gets their data from the trust provider and evaluates it against the policies that you set for the application. Verified Access grants access to the requested application only if the user meets your specified security requirements.
In addition, Verified Access logs every access attempt, to help you respond quickly to security incidents and audit requests.

Pricing
There are two components that determine your Verified Access bill: 1) hourly charges for associated applications and 2) per GB charges for data processed. You also incur standard AWS data transfer charges for all data transferred using Verified Access.
Application hours
You are charged per hour for each application associated with Verified Access. For example, if you associate 10 applications with Verified Access, each for an hour, you will be charged per hour 10 application hours. Each partial application hour consumed is billed as a full hour.
GB of data processed
You are also charged per GB for data processed by Verified Access. When users request access or connect to your applications, Verified Access processes the data flowing between users and the application. For example, if all your applications using Verified Access require 10 GB of total data processing you will be charged for that 10 GB data processed.
Pricing table
| Region(US East – Ohio) | ||
| Tiered pricing for application hours | Price | |
| 1- 148800 app-hours(covers up to 200 apps in a month) | $0.27/hr | |
| 2- 148800+ apps-hours | $0.20/hr | |
| Per GB of data processed | $0.02 | |
Note: 200 apps associated for [31] days equals 148,800 app-hours
Key components of Verified Access
Verified Access Instances
A Verified Access instance is an AWS resource that helps you organize your trust providers and Verified Access groups.
Trust providers for Verified Access
A trust provider is a service that sends information about users and devices, called trust data, to AWS Verified Access. Trust data may include attributes based on user identity such as an email address or membership in the “sales” organization, or device management information such as security patches or antivirus software version.
Verified Access supports the following categories of trust providers:
- User identity – An identity provider (IdP) service that stores and manages digital identities for users.
- Device management – A device management system for devices such as laptops, tablets, and smartphones.
Verified Access Group Provider
An AWS Verified Access group is a collection of Verified Access endpoints and a group-level Verified Access policy. Each endpoint within a group shares the Verified Access policy. You can use groups to gather together endpoints that have common security requirements. This can help simplify policy administration by using one policy for the security needs of multiple applications.
For example, you can group all sales applications together and set a group-wide access policy. You can then use this policy to define a common set of minimum security requirements for all sales applications. This approach helps to simplify policy administration.
When you create a group, you are required to associate the group with a Verified Access instance. During the process of creating an endpoint, you will associate the endpoint with a group.
Verified Access Endpoint
A Verified Access endpoint represents an application. Each endpoint is associated with a Verified Access group and inherits the access policy for the group. You can optionally attach an application-specific endpoint policy to each endpoint. There are two types of Endpoint in Verified Access which are network interface and load balancer.
Verified Access policies
AWS Verified Access policies enable you to protect access to your corporate applications hosted in AWS. They are written in Cedar, an AWS policy language. With Verified Access, you can express policies that use the trust data from the trust providers you configure, such as corporate identity providers and device security state providers.
Demo
Lets create a demo for Verified Access
Prerequisites
The following are the prerequisites for this tutorial:
- To demonstrate this example for using Verified Access, we will be using two AWS accounts. One account will host your target application, and the Verified Access resources will be created in the other account.
- Enable AWS IAM Identity Center (successor to AWS Single Sign-On) in the AWS Region that you’re working in. You can then use IAM Identity Center as a trust provider with Verified Access. For more information, see Enable IAM Identity Center in the AWS IAM Identity Center (successor to AWS Single Sign-On) User Guide.
An application running behind an internal load balancer in an AWS account. The example application domain name we’ll use is www.myapp.example.com.